After two years of virtual events, I was thrilled to attend KB4-CON 2022, run by KnowBe4, Inc., which took place in the Gaylord Palms Resort & Convention Center in Orlando, Florida, USA. KnowBe4 Inc. is the provider of the world’s largest security awareness training and simulated phishing platforms.
KB4-CON 2022 was a packed conference with approximately 2,000 in attendance and a great lineup of speakers. The conference theme this year was focusing on three core components of what KnowBe4 believes are key to a strong security posture which they call the ABCs – awareness, behavior, and culture. More information on this conference is found online at: https://www.knowbe4.com/kb4-con
Following a welcome from KnowBe4 CEO Stu Sjouwerman, Nicole Perlroth, cybersecurity and digital espionage reporter for The New York Times delivered a riveting talk entitled “This Is How They Tell Me the World Ends”. This session highlighted thrilling untold stories of the cyberweapons market – the most secretive, invisible, government-backed market on earth – and a terrifying first look at a new kind of global warfare. It was wonderful to see Winn Schwartau, as well, author of the Best Cybersecurity Book of All Time – Analogue Network Security, at KB4-CON 2022. Winn will be keynoting our conference for CISOs and innovators like KnowBe4, who are helping us get one step ahead of the latest threats, in October this year.

I was once again impressed with the information imparted from great speakers like Nicole Perlroth, Perry Carpenter, Roger Grimes and many others, with excellent opportunities for networking with IT security peers. Beyond the excellent product updates and demonstrations, I was intrigued with the new model which will most likely become a de facto industry term. Before I discuss it, let’s look at a recent similar industry innovation – XDR.
By now we have all heard of XDR this is a term coined by Nir Zuk of Palo Alto networks in 2018, which stands for extended detection and response. XDR helps improve the malware detection over traditional antivirus solutions by offering improved prioritization of threats giving executives higher visibility in their cyber security and risk posture.
Now, enter HDR.
This may be the first time you’re hearing this term, which stands for human detection and response. One of the challenges for most organizations is to build a strong security culture. Stu Sjouwerman, Founder & CEO of KnowBe4, calls this the ABCs of HDR – awareness, behavior, and culture.
According to Perry Carpenter, Chief Evangelist & Strategy Officer and Kai Roer, Chief Research Officer of KnowBe4, Inc., Security Culture is defined as “The ideas, customs and social behaviors of an organization that influence its security.”
In our annual Black Unicorn Report, I’ve coined the phrase PANCCD – where the top of this infosec pyramid is people (aka humans). KnowBe4 understands this and has created HDR to help us better measure and quantify risk based on human behavior detection of anomalous behavior in the response to that behavior this goes way beyond traditional anti-phishing and security awareness training.
If you ask yourself, what are you doing to ensure that the right security knowledge, beliefs, and value systems are woven throughout the fabric of your organizational culture? And, in regards to this innovation of HDR, you might want to take a look at the new book by Perry and Kai, entitled:
The Security Culture Playbook
 A concrete blueprint for producing real change, reducing risk, and proactively managing your company’s exposure to cybersecurity threats. You’ll also find:
A concrete blueprint for producing real change, reducing risk, and proactively managing your company’s exposure to cybersecurity threats. You’ll also find:
- Revealing interviews from security culture thought leaders in a variety of industries.
- Strategies for bringing all the security culture pieces together into a coherent program.
- Actionable and modern insights from sociology and other academic disciplines.
- In-depth explanations of how to implement and shape behavioral outcomes, foster social pressures, and create positive patterns.
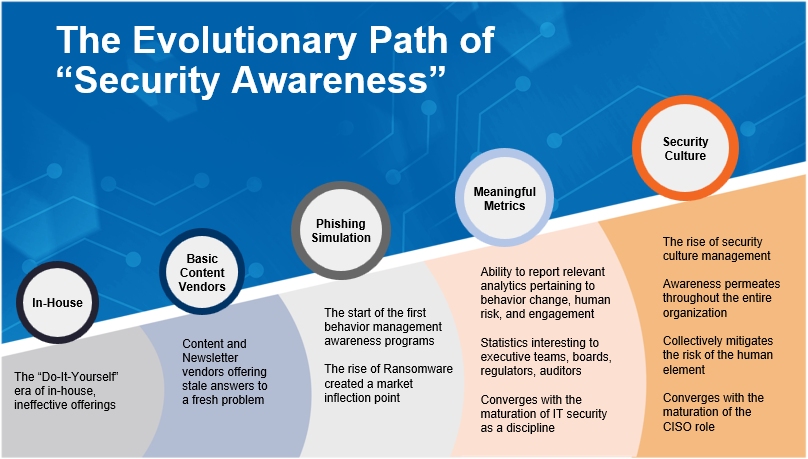
People are vulnerable, we humans make mistakes, so to create an improved security culture in an organization one should look to this new model – HDR. It also includes CMI’s – cultural maturity indicators. While this human factor is traditionally ignored as part of the security stack, it’s now the 8th layer and KnowBe4 is making it more actionable and measurable by having CMI’s – we now gain a data-driven advantage.
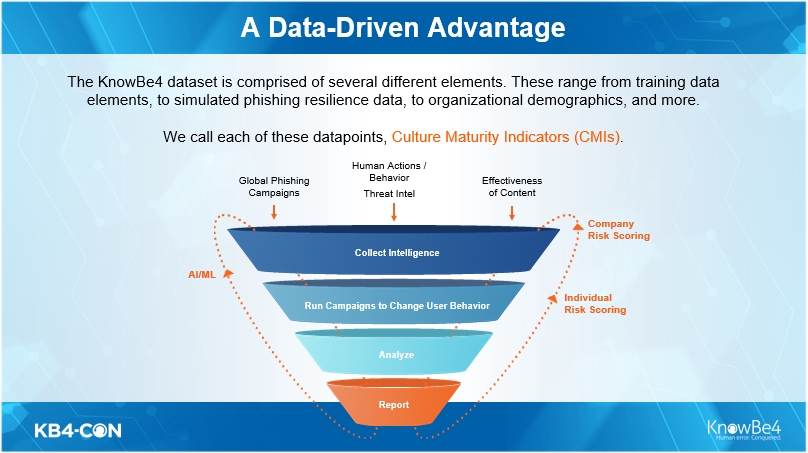
Example CMI’s including Security Awareness Training, Phishing and Simulated Phishing Testing and much more as you track and report on employee/user behaviors. This is a pivotal moment for CISOs and their infosec teams – to finally include people in the equation in a quantifiable way. Whether you know it or not, your employees ABC’s are all part of your Security Culture Maturity Module (SCMM). This is also part of the HDR platform:
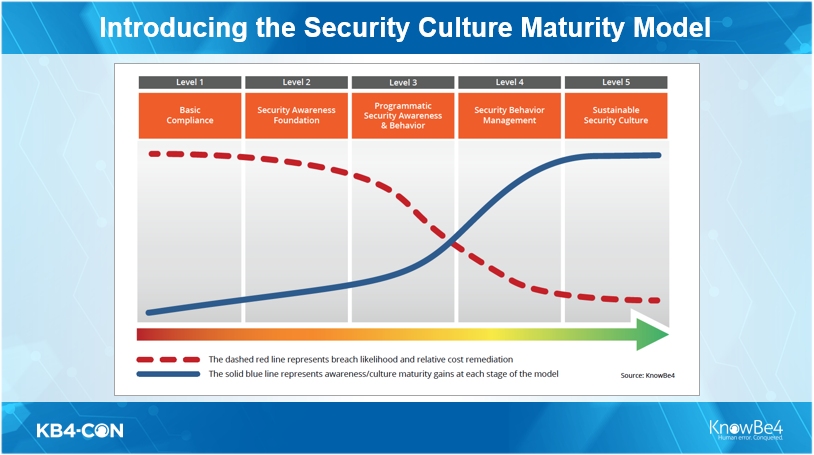
Keep a keen eye on KnowBe4, their HDR, SCMM and CMI’s – this will be game changing.
Gary S. Miliefsky, fmDHS, CISSP
Publisher, Cyber Defense Magazine
Chairman & CEO, Cyber Defense Media Group
P.S. By the way if you’re looking for phishing, security awareness, training, password, email security and other great tools, you can find all the freebies KnowBe4 offers at the following link: https://www.knowbe4.com/free-it-security-tools
FAIR USE NOTICE: Under the “fair use” act, another author may make limited use of the original author’s work without asking permission. Pursuant to 17 U.S. Code § 107, certain uses of copyrighted material “for purposes such as criticism, comment, news reporting, teaching (including multiple copies for classroom use), scholarship, or research, is not an infringement of copyright.” As a matter of policy, fair use is based on the belief that the public is entitled to freely use portions of copyrighted materials for purposes of commentary and criticism. The fair use privilege is perhaps the most significant limitation on a copyright owner’s exclusive rights. Cyber Defense Media Group is a news reporting company, reporting cyber news, events, information and much more at no charge at our website Cyber Defense Magazine. All images and reporting are done exclusively under the Fair Use of the US copyright act.
Credit: Source link


Comments are closed.