Advancing Risk Management and Stemming the River of Risk by Adopting the Consistent Taxonomy of Cybersecurity Threats – Cybersecurity’s “Lingua Franca.”
By Charlie Miller, Senior Advisor, Shared Assessments, CTPRP, Distinguished Ponemon Fellow
Companies have been assessing their risks for ages so that they can mitigate them. When companies began to outsource, they faced new risk challenges because they didn’t have much visibility into the control adequacy of the third parties they used. Technology, digital transformation, networking connectivity, and the Internet have grown into a commercial space over the past 25 years, and companies — and their third parties — now face a complex ecosystem of cybersecurity issues. As a cybersecurity risk professional, you know them all.
Except maybe for the new ones somebody is concocting right now.
It’s one thing to monitor the cyber control activity — and threats — for one organization. Outsourcing drives cyber security monitoring to a new level, because suddenly it’s not just your own organization you’re worried about. You have to be aware of the most critical threats for your third-party suppliers and service providers as well because compromises there may affect you. A large company might have 40,000 suppliers, or more. Monitoring all of that is a tall order.
Enter Continuous Monitoring
Some third parties are directly connected to corporate networks, and some are not, but all have increased cyber security exposures. Security Rating Services (SRS) have arisen recently. Their solutions, usually provided as Software-as-a-Service (SAAS), continually watch over their own organization’s cyber hygiene as well as a host of third parties and potential third parties — examining events and vulnerabilities for which they provide a rating. The offerings and ratings of SRS providers are similar, but they vary in terminology, price and pricing models, the events they monitor, their alignment with external security frameworks and standards, in customer interface, data sources, methods for gathering and reporting cybersecurity control weaknesses information, and in many other ways. Basically, they’re all different.
That diversity gives you a rich variety of choices but makes it difficult to compare services and ensure that cyber hygiene monitoring aligns with your control requirements.
There is another and perhaps more subtle aspect to all this difference between organizations and the providers they use. Every IT and cyber security manager must communicate upwards in the organization, eventually all the way to the board of directors. Clarity in that communication affects funding, staffing, and equipment as well as security per se.
What was needed was a lingua franca — a common language that describes the world of monitored cyber threats. This would allow organizations to:
- Achieve a better understanding of how events monitored by SRS align with the outsourcer’s control requirements, and vice versa.
- Compare the services offered by several SRS providers.
- More easily communicate any issues identified by the SRS and develop mitigation approaches to correct them.
- Clearly communicate across the third-party risk management ecosystem, which helps boards and leadership teams evaluate cyber threats to the business and align appropriate resources. It is important to have a common terminology, especially when communicating to non-technical people. In an environment with global supply chains, this clear communication becomes even more important.
The lack of such a lingua franca — a consistent taxonomy of cybersecurity threats — has posed problems for organizations, third parties, and SRS providers.
So, What’s the Problem?
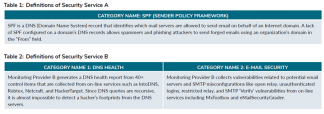
Table 1 and Table 2 show an example of a common yet specific terminology problem. A company wants to assess a vendor to ensure that the vendor’s email servers cannot be used for phishing attacks targeting the outsourcing company. Specifically, the outsourcer wants to know if the vendor has enabled the Sender Policy Framework (SPF) on their network. SPF is a Domain Name Service (DNS) configuration that organizations can enable to help stop attackers from impersonating an organization’s email addresses.
When reviewing Security Rating Service A’s alert category, it is easy to spot the reference to SPF because SPF is specifically listed. However, in Security Rating Service B’s solution, it is hard to tell if either Category 1 or Category 2 matches the outsourcers need for SPF monitoring.
A Group of Rivals
Shared Assessments is a member-driven organization that has developed and promoted standardized resources for corporate risk assessment (not just cyber risk assessment) for over a decade. SA members — including SRS providers such as 23Advistory, BitSight, Black Kite, Panorays, RiskRecon, and Security Scorecard — worked through Shared Assessments to create the common taxonomy with which they could describe their varied offerings. The taxonomy establishes consistent language, practices, and reporting structures for complex cyber events and vulnerabilities, and removes the potential for ambiguities. Each of the “rivals” sees advantages for themselves and their clients.
The World Economic Forum and NIST are both considering leveraging the taxonomy to ensure consistency with their own frameworks and terminology.
The taxonomy itself takes no stance on the relative importance of any one event over any other. What is required is that an event is currently being monitored by someone, in some way, in the real world. The events are described in the adverse to avoid duplication. For example, one SRS provider may say “the XYZ patch is missing — that’s bad” and provide a lower score while another provider may say “the XYZ patch is present — that’s good” and provide a higher score. The taxonomy always describes the XYZ patch in its adverse form to avoid describing the condition twice.
Among the key definitions in The Unified Third Party Continuous Monitoring Cybersecurity Taxonomy are the following:
- Monitoring Surface: Cataloging of technical or organizational characteristics that help identify the presence of other events or states, such as domain names, Internet Service Providers, email service providers, and IP addresses to help stakeholders better understand how SRS providers identify events. This category of definitions includes those for fingerprint values and attach surface variables such as those associated with assets that can be used to understand the scope, strengths, and weaknesses of an organization’s business and technical environment. Surface variables can determine whether a control or vulnerability does or does not exist.
- Events: Actual cybersecurity vulnerabilities indicating a lack of a control that a monitored organization may be exposed to. Domains and categories include:
- Business Intelligence: The range of categories such as reputational exposure, business metric changes, security incidents, and other events.
- Indicators of Compromise: Including active and passive signals. Active, such as dangerous activity that is occurring and picked up in real-time or near-real-time; passive, such as lists, credential leaks, and exposed information.
- Vulnerabilities: Defining the full constellation of areas of potential risk across the spectrum of cyber elements such as DNS, email, web applications, remote access, practices, network services, client applications, network, and cloud security.
A “River of Risk”
One of the biggest problems seen by Shared Assessments’ “group of rivals” is slow patching cadence. With 40–50 billion (with a B) vulnerabilities cropping up per week, slow patching continues to be a major problem. In descending order are other issues such as Distributed Denial of Service (DDoS) attack mitigation, End-of-Life systems remaining online, and systems online after End-of-Support.
According to the CSC 2021 Domain Security Report on Forbes Global 2000 companies:
- 81% did not use Registrar-Lock Protocol
- 50% did not use DMARC (Domain-based Message Authentication, Reporting & Conformance)
- 89% did not use DKIM (DomainKeys Identified Mail, an email authentication method to detect forged sender addresses)
- 60% of “homoglyph” domains (to catch typos like “amuzon”) were registered in the last two years.
According to the rivals, simple and effective mitigations include:
- 3 adoption
- HTTP Strict-Transport-Security response header (HSTS headers)
- OWASP Top 10 (updated September 2021)
- Center for Internet Security (CIS) Critical Security Controls (v8 updated May 2021)
The taxonomy is an industry effort and a living document, maintained by Shared Assessments. It is the most recent result of a two-phase cooperative project let by the Shared Assessments Continuous Monitoring Working Group, established in 2017, which galvanized practitioners from over 55 member organizations. The first phase was published as an article in 2019, “Creating a Unified Continuous Monitoring Cybersecurity Taxonomy: Gaining Ground by Saying What’s What.” The second phase is the taxonomy itself.
A copy of the Shared Assessment Unified Third Party Continuous Monitoring Taxonomy can be obtained for free and here is where the SRS firms explain the benefits of the Webinar Cybersecurity Taxonomy for Continuous Monitoring.
About the Author
 Charlie Miller, Senior Advisor, Shared Assessments, CTPRP, Distinguished Ponemon Fellow – Charlie is a frequent speaker and a recognized expert in Third-Party Risk. His key responsibilities include expanding the Shared Assessments Third-Party Risk Management membership-driven program, facilitating thought leadership, industry vertical strategy groups, continuous monitoring / operational technology working groups, and IoT research studies.
Charlie Miller, Senior Advisor, Shared Assessments, CTPRP, Distinguished Ponemon Fellow – Charlie is a frequent speaker and a recognized expert in Third-Party Risk. His key responsibilities include expanding the Shared Assessments Third-Party Risk Management membership-driven program, facilitating thought leadership, industry vertical strategy groups, continuous monitoring / operational technology working groups, and IoT research studies.
He joined Shared Assessments in 2015 and has been in the third-party risk space for over 15 years. He has vast industry experience, having set up and led third-party risk management and financial services initiatives for several global companies.
Charlie was the Director of Vendor and Business Partner Risk Management at AIG and implemented third-party risk management programs at Bank of Tokyo Mitsubishi (BTMU). He held multiple leadership roles at Merrill Lynch & Co., Inc. overseeing the company’s global vendor management program and a Director of Technology Audit. He led a financial services practice unit as a consulting partner at Deloitte, focusing on technology outsourcing, risk management, and cost control. He began his career at IBM as a systems engineer.
Charlie is a Distinguished Fellow of the Ponemon Institute, a Certified International Privacy Professional, and Certified Third-Party Risk Professional.
Connect with Charlie via email or through LinkedIn, and at https://sharedassessments.org/
FAIR USE NOTICE: Under the “fair use” act, another author may make limited use of the original author’s work without asking permission. Pursuant to 17 U.S. Code § 107, certain uses of copyrighted material “for purposes such as criticism, comment, news reporting, teaching (including multiple copies for classroom use), scholarship, or research, is not an infringement of copyright.” As a matter of policy, fair use is based on the belief that the public is entitled to freely use portions of copyrighted materials for purposes of commentary and criticism. The fair use privilege is perhaps the most significant limitation on a copyright owner’s exclusive rights. Cyber Defense Media Group is a news reporting company, reporting cyber news, events, information and much more at no charge at our website Cyber Defense Magazine. All images and reporting are done exclusively under the Fair Use of the US copyright act.
Credit: Source link


Comments are closed.