In a Latest Machine Learning Research, Researchers Question the Ease of Leaking Data from Inverting Gradient Highlighting Dropout is not Enough to Prevent Leakage
To develop a shared machine learning model, federated learning algorithms were created to take advantage of the cooperative usage of dispersed data. Systemic privacy issues can be reduced since participating customers do not share training data. However, recent research demonstrates that by reconstructing sensitive data from gradients or model states that are shared during the federated training, the privacy of participating clients might be jeopardized. Iterative gradient inversion assaults enable the most adaptable reconstruction strategies. These techniques enhance randomly initialized dummy pictures to produce dummy gradients that are identical to the gradient of the targeted client.
For example, they are increasing the batch size or the number of local training iterations and changing the input data to include perturbation or input encryption. Apart from this, changing the exchanged gradient information to include noise, compression, pruning, or applying specially created architectural features or modules are all examples of defense strategies against such attacks. However, most defensive systems force a trade-off between model functionality and privacy.
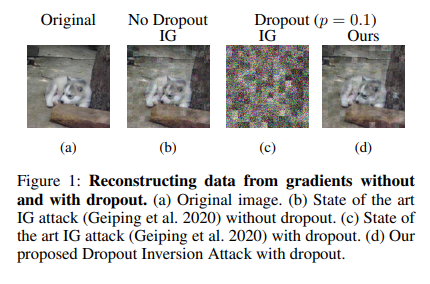
Dropout is a regularisation method used in deep neural networks to reduce overfitting. While dropout can improve neural network performance, current studies indicate that it may shield shared gradients from gradient leaking. These discoveries served as our inspiration, and the researchers used recurrent gradient inversion assaults to demonstrate that the stochasticity generated by dropout does shield shared gradients against gradient leaking. However, according to our argument, this defense is only visible because the attacker lacks access to the particular implementation of the stochastic client model used for training.
Furthermore, the researchers contend that an attacker can use the shared gradient information to sufficiently simulate this particular instantiation of the client model. They develop a unique Dropout Inversion Attack (DIA) that optimizes for client input and the dropout masks used during local training to expose the weakness of dropout-protected models. The following summary of our contributions: • Using a methodical approach, they demonstrate how dropout during neural network training appears to stop repetitive gradient inversion assaults from leaking gradient information. •, Unlike other assaults, the unique approach they develop correctly reconstructs client training data from dropout-protected shared gradients.
Be aware that any other iterative gradient inversion technique may be extended using the elements of our suggested method. • The researchers conduct a thorough, systematic evaluation of their assault on three increasingly complicated image classification datasets, two CNN-based (LeNet, ResNet) and dense connection-based (Multi-Layer Perceptron, Vision Transformer) model architectures (MNIST, CIFAR-10, ImageNet).
There is a GitHub repository shred by the appearing authors in the reference section named Inverting Gradients. How easy its to break federated systems. The code implementation on the repository has the technique to regenerate data from gradient information.
This Article is written as a research summary article by Marktechpost Staff based on the research paper 'Dropout is NOT All You Need to Prevent Gradient Leakage'. All Credit For This Research Goes To Researchers on This Project. Check out the paper and github link. Please Don't Forget To Join Our ML Subreddit
![]()
Content Writing Consultant Intern at Marktechpost.
Credit: Source link

Comments are closed.