Controlling Cyber Risks and Fraud by Risk Assessment
By Hakan Kantas, Senior IT Director
We are trying to protect all the Internet connected systems, users, network and other related structures with the renewed and evolving regulations, new applications, processes and services that come with new technologies, in parallel with the developing technology and innovations, and we call this as Cyber Security. The risks that come with so many interconnected structures need to be analyzed, and this is where the Cyber Security risk assessment comes to the forefront.
Digital Transformation, which is one of the most popular topics of the last period, attracts attention especially in societies that are open to innovation and like to adapt and use the latest technologies quickly. Institutions that want to adapt to new technologies and bring their customers into this area are quickly starting the digital transformation process. However, each new technology brings with it new and often unknown risks. Managing these sometimes unknown risks and preventing the loss of information, today’s most valuable asset, is as popular as digital transformation and as important as cybersecurity. These new technologies and applications are one of the reasons why cybersecurity has become so popular in recent years.
As the leader of the team that established and implemented the IT risk management methodology in my institution years ago, I would like to express that risk management is one of the fundamental building blocks of cybersecurity. At first glance, you may not see a direct relationship between these two concepts, or you may not understand why such a study is needed. However, you will understand how the methodology I will explain in the rest of this article will make a difference in terms of fraud prevention.
At this stage, it would be right to make a statement to those who ask, “Let’s run cybersecurity directly, and what is the need for risk analysis.” It is not generally known where the new technologies and applications introduced and implemented through digital transformation have gaps, problems and risks. Even if there is general awareness, existing risks may increase or shift during the process of implementation and adaptation from institution to institution. The only way to uncover these threats and vulnerabilities is to conduct a comprehensive risk assessment study. In this way, unknown potential vulnerabilities can be identified before an incident occurs and the necessary precautions can be taken.
Security and system vulnerabilities in new products and technologies can, to some extent, be uncovered by numerous cybersecurity tools. However, since these are new products, it takes time for existing security products to adapt and provide more serious controls. In the meantime, the greatest risk is in the process of adapting and adapting security products to new technologies. Cybersecurity risk assessment, which can prevent this, provide stronger measures, and is not very difficult to implement, can play a redeeming role here.
Cybersecurity risk assessment is a very critical aspect because this assessment makes it possible organizations to identify and prioritize determined critical risks. You will to create action plans to mitigate identified risks with this methodology. Without a risk assessment process in place, organizations may be vulnerable to data breaches, phishing and cyberattacks which can result in significant financial and reputational damages. A regular cybersecurity risk assessment is essential for any organization to be able to control potential vulnerabilities and comply with new regulations and laws. This routine study will not only reveal potential vulnerabilities and threats in the long run, but will also provide a more mature continuation of future evaluations as it will provide a basis for the next study.
We will begin our work by first discussing what the cybersecurity threats are. As mentioned above, the purpose here is not to list all the threats, but to convey the general working methodology with an example set. So we’ll start the methodology by listing the most common threats overall.
- Phishing
- Ransomware
- Malicious Software
- Social Engineering
- DOS/DDOS Attacks
Step-1 – Determine and Prioritize Assets and Value
Today, even the largest organizations do not have unlimited resources. Every work, project, product, in short, every process has a certain budget and resource. Based on this awareness, we need to set out by knowing that we have a limit for the risk study we will carry out.
Within the framework of the boundaries and limits we draw, we must first identify our most valuable assets. After creating the framework for this, you can start preparations by listing the assets in that area. In fact, having a catalog of all assets and categorizing them as very critical, critical, important, unimportant, etc. is the most critical work and the basic building block that needs to be addressed as the first step. Preparing a catalog of all assets as a first step is not an easy task. As we mentioned above, we should create an inventory with a defined scope, otherwise keeping the scope too broad may cause you to miss the target while trying to reach an endless inventory. Depending on the scope, in addition to the titles listed below, Cloud solutions such as Software-as-a-Service (SaaS), Platform-as-a-Service (PaaS), and Infrastructure-as-a-Service (IaaS) can also be included in this assessment.
- Information security policies
- Information Technology Architecture
- End Users
- Support Staff
- Architectures that show information flow
- Technical and physical checklists
- Criticality information
- Technical Data
- Software
- Hardware
After completing the extraction of assets according to the scope we have determined, we can determine the criticality of those assets by asking the sample questions below. Of course, you can elaborate these questions within the scope of the area you work in, how detailed the risk study is aimed to be, the scope and diversity of the asset list.
- If I lose this information, will I experience a regulatory or legal event?
- Will the loss of this data affect my institution financially?
- Without this data, can the institution survive, can the work be done, can the operation be maintained?
- How critical is this information to my competitors?
- Which processes and structures are most vulnerable to data loss?
Step-2: Identifying vulnerabilities and cyber threats
One of the most critical points of risk analysis is to identify potential threats and vulnerabilities from the broadest perspective, without overlooking anything. Identifying the threats that can cause vulnerabilities and determining which vulnerabilities they are the source of will form the inventory we need to uncover in the second step. At this point, we immediately think of spoofing software and hackers. However, there are many threats that do not come to mind. For example, when you see natural disasters among the items below, you may say “but this is not a cyber attack”. What is meant here is whether the systems become vulnerable to a possible cyber attack after a natural disaster. It is important to look at the issue from this perspective.
Let us list a few of them:
- Human Error: Has the staff in your organization been informed about cyber-attacks and their types?
- System Failures: Are the systems that hold and process your most important data regularly checked and maintained, and are they actively monitored?
- Natural disasters: How much can disasters such as earthquakes, storms, floods, fires affect the structures and systems that hold your critical data? It should be kept in mind that as a result of such a disaster, not only people but also the hardware and systems that hold this data may be affected.
- Unauthorized Access: There may be unauthorized access to data due to the success of one of the cyber attacks on the organization.
- Misuse of authorization: The risk that the users you authorize may use the data for different purposes or take it out of the organization for malicious purposes should not be forgotten.
Step-3: Risk Assessment
This is the point we have been trying to get to from the very beginning. In other words, this is the stage where cyber security risk analysis is done.
The risk assessment of the information and inventory we collected in the first two steps, that is, the likelihood and severity of the events mentioned, is evaluated at this stage.
Different organizations and methodologies make different levels of assessment here. While some standards assess at 3 levels such as low, medium and high, the general practice consists of 5 levels: very low, low, medium, high and very high. It would not be appropriate to use a statement that says, “Use this, this is correct”. Because many factors such as the size of the organization, the area, the criticality of the data, awareness of cyber security, measures, human resources, etc. include criteria that will affect this decision.
Severity and Likelihood should be determined for each identified risk. As I mentioned above, the general practice is to evaluate both topics in 5 stages as you can see in the table below. For each risk, severity and likelihood values are determined individually and multiplied to obtain the risk rating.
Risk Rating = Severity X Likelihood
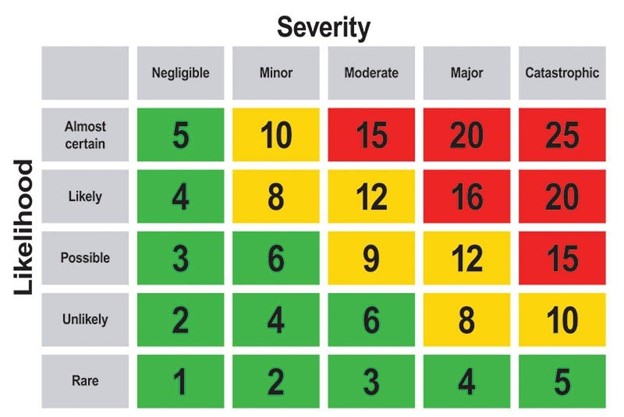
The risk ratings that emerge from this step can be named in different ways. Some may call these green, yellow and red areas Low, Medium and High, while others may call them Insignificant, Acceptable and Unacceptable.
While different organizations generally categorize the degree of risk in 3 categories, some consider risks with a very high severity and likelihood, i.e;
Likelihood 5 X Severity 5 = Risk Rating 25
They may categorize risks as NOT TOLERABLE in a completely separate way. This assessment may vary depending on the scope, method and methodology.
Step-4: Control Step
In this step, we determine the controls for our risks that we have uncovered in the 3 steps above and determined the degree of risk.
When we say control, we are talking about all kinds of actions that will ensure that the risk does not materialize. All kinds of measures to be taken to prevent potential risks from materializing, to prevent them, or to reduce the likelihood of the risk even if we cannot completely prevent it in any way, should be considered under this heading. One of the most critical steps of this work is to examine each risk individually and to produce controls by evaluating them by the relevant teams.
A few examples of controls can be given as follows:
– Data in the transfer or storage phase
– Installing and using special applications such as anti-malware, anti-phisting beyond anti-virus applications,
– Firewall regulations, rules, measures,
– Regular password change and secure password,
– And I think most important of all; Education, education, education…
Step-5: Monitoring, Evaluation and Reporting
These studies, which we have briefly mentioned above, require serious knowledge, labor, effort and analysis. We have done all this work and completed our Cyber Security Risk Assessment. So, what happens now?
First of all, a report should be prepared that includes details such as all identified risks, risk assessments, risk categories and controls taken/planned to be taken. The report should be forwarded to senior management and used as input for management decisions in areas such as budget, investment, policies and procedures.
With this study, you have also created a general operation and security map such as where your critical data is located, by whom it is used, what risks it carries, how and where it is processed. You can and should use this map both in projects or large-scale studies carried out within Information Technologies and in critical decisions to be taken by business units.
After running the process several times, maturity and awareness will increase even more, and after a while you will see that your cyber security risk analysis work has reached a much better and mature point. Of course, in this process, you should not ignore the improvement of your cyber security risk assessment process, if necessary, in line with the needs and technological developments.
I wish you good luck to creating safer and healthier working environment by applying the above method in your organization..
About the Author
 Hakan Kantas is an IT Director. He started his professional career in 1993 in the IT department of Pamukbank, Turkey. He was the CIO of Vaillant Group in 2007-2008. He has been working for a private bank in Turkey since 2008. Currently, he’s Senior Director of IT Continuity Management Department and he’s responsible of following areas; Operational Resilience, Risk ve Cyber Security related to Resilience, IT Continuity Management, Disaster Recovery, Crisis Management, IT Capacity and Performance Management, Data Management and GDPR. He is an IEEE Senior Member, member of ISACA (Gold Member), member of Association for Computing Machinery (ACM), member of Information Technology Association, and member of Business Continuity Institute (BCI) and former board member of itSMF-Turkey Chapter.
Hakan Kantas is an IT Director. He started his professional career in 1993 in the IT department of Pamukbank, Turkey. He was the CIO of Vaillant Group in 2007-2008. He has been working for a private bank in Turkey since 2008. Currently, he’s Senior Director of IT Continuity Management Department and he’s responsible of following areas; Operational Resilience, Risk ve Cyber Security related to Resilience, IT Continuity Management, Disaster Recovery, Crisis Management, IT Capacity and Performance Management, Data Management and GDPR. He is an IEEE Senior Member, member of ISACA (Gold Member), member of Association for Computing Machinery (ACM), member of Information Technology Association, and member of Business Continuity Institute (BCI) and former board member of itSMF-Turkey Chapter.
Hakan can be reached at; hakkan@gmail.com, hakan.kantas@ieee.org, hakkan@hakankantas.com and https://hakankantas.mystrikingly.com/
Credit: Source link


Comments are closed.