By Diem Shin, Product Marketing Lead at Telos Corporation
Today’s organizations are cloud-centric and are more connected than ever before. Many organizations are ladened with legacy systems and complex IT infrastructure, making it more challenging to secure but more attractive for cyber-criminal syndicates seeking quick financial gains. A slew of high-profile, devastating attacks on critical infrastructure organizations — Colonial Pipeline, JBS USA, and Kaseya — have left organizations scrambling to figure out how to bolster defenses to handle the ever-increasing cyber threat.
According to a recent study conducted by Vanson Bourne, an independent market research agency for the technology sector, 83 percent of organizations have experienced a cyber attack in the past two years that breached the network but did not gain access to the critical IT assets, where 50 percent reported that hackers were able to reach their critical IT assets. This finding is corroborated by numerous other studies, including research conducted for S-RM that found 61 percent of organizations have suffered a serious cyber incident in the last three years. While the figure is slightly lower than that of Vanson Bourne, this study only refers to “serious” cyber incidents, while the research cited above was broader in nature. With many organizations clearly struggling to defend their networks from cyber attacks, there’s no room for complacency when it comes to protecting critical IT assets.
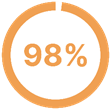 of organizations fear an attack on their critical IT assets within the next six months.
of organizations fear an attack on their critical IT assets within the next six months.
What is considered a critical IT asset?
A critical IT asset is one whose loss or theft would be catastrophic not only for the organization but also for the wider society. According to Vanson Bourne, critical IT assets fall into one of the three categories:
- Operational tools: Fundamental to daily business, compromise of these tools is likely to impact the ability of an organization to generate revenue and provide services to customers, patients or students. For example, telehealth and remote medicine platforms are essential components of healthcare organizations to provide services to their patients.
- Security systems: Systems organizations have in place to protect customers, IT networks, and physical premises. They play a crucial role in ensuring organizations can operate securely; a compromise of the system would open doors for hackers to install malware to exfiltrate data or as a precursor to a ransomware attack.
- Databases: Containing sensitive, high-value information such as customer or employee data or intellectual property.
Critical IT assets vary across the different sectors:
| Sector: | Banking, financial services, and insurance | Healthcare and life sciences | Energy, oil/gas, and utilities | K-12 education | Higher education |
| Asset to secure: | Transaction infrastructure | Telehealth and remote medicine platforms | Field operations | Cyberbullying protection systems | Digital learning tools, platforms, and communications |
With the heightened concern around protection for critical IT assets, are current security tools sufficient to ward off further attacks?
Organizations are currently using a variety of tools to protect their IT networks. The traditional security toolkit includes antivirus programs (42 percent), identity and access management (40 percent), encryption tools (40 percent), and a firewall (40 percent) – all designed to keep out unauthorized users and limit the damage if there is a breach. However, if a bad actor has breached the perimeter and gained access to the network, all assets including critical IT assets are visible and vulnerable to attacks.
There are additional concerns that organizations have around the tools that are currently used to protect their critical IT assets. The primary concern is that internal users have too much access to these assets. In this case, the stolen credentials of a user with unlimited access to the network could result in a catastrophic attack with devastating implications.
Adding to the challenges of protecting critical IT assets, 75 percent of organizations believe that their IT and IT security staff are not completely prepared to deal with the increase in attacks. As cyber-attacks increase in frequency and complexity, they will become inherently harder to defend against. And organizations need to assess their security posture and ensure that they have the right tools in place to ward off future attacks.
Segmentation of Critical Assets is the first step
 of organizations believe they need to improve their ability to prevent an attacker from accessing critical IT assets in the event of a breach.
of organizations believe they need to improve their ability to prevent an attacker from accessing critical IT assets in the event of a breach.
To achieve that extra measure of protection, organizations need to look beyond the traditional security tools that focus on keeping out unauthorized users to include tools that protect assets within the network.
Most organizations (70 percent) are segmenting critical IT assets so that they are protected with separate, specific tools. Segmentation enables organizations to provide damage control and prevent a small breach from becoming a massive data breach. Segmenting critical IT assets provides another obstacle to threat actors looking for an easier target.
While segmentation offers many benefits, 93 percent of organizations believe that the current tools used to protect segmented assets are not sufficient to defend against cyber-attacks and they plan to implement additional solutions to protect critical IT assets.
Network Obfuscation – Secret Weapon for Protecting Critical IT Assets
One of these tools is a network obfuscation solution. Network obfuscation is mentioned as one of the top three tools organizations plan to implement in the next two years to protect critical IT assets. Network obfuscation tools hide network assets by eliminating IP addresses from the public internet and from cyber adversaries. Many solutions also combine IP obfuscation, multi-layer encryption, and dynamic IP routing to ensure that network assets remain anonymous. With network obfuscation, attack surface areas are eliminated, thus minimizing or eliminating the risk of cyber-attacks.
Combined with segmentation, network obfuscation enables organizations to provide a more stringent security protocol for critical assets. For those who have been kept awake at night by concerns of hackers reaching their crown jewels, an obfuscation solution that hides their presence from the internet can help them sleep better. Over the next two years, 35 percent of organizations plan to invest in network obfuscation as part of their toolkit to protect their critical IT assets.
Read the full report, Evolution of Critical IT Asset Protection, by Vanson Bourne, commissioned by Telos.
About the Author
 Diem Shin joined Telos in 2021 and serves as product marketing manager for Telos Ghost, the company’s cloud-based managed attribution products and services business. Diem has over 15 years of experience in developing and launching software and SaaS solutions for global technology companies. Prior to joining Telos, Diem worked for technology companies including Fugue, Verisign, Clarabridge, Neustar, and Ericsson.
Diem Shin joined Telos in 2021 and serves as product marketing manager for Telos Ghost, the company’s cloud-based managed attribution products and services business. Diem has over 15 years of experience in developing and launching software and SaaS solutions for global technology companies. Prior to joining Telos, Diem worked for technology companies including Fugue, Verisign, Clarabridge, Neustar, and Ericsson.
Diem Shin can be reached online at https://www.linkedin.com/in/diemshin/ and at our company website https://www.telos.com/
FAIR USE NOTICE: Under the “fair use” act, another author may make limited use of the original author’s work without asking permission. Pursuant to 17 U.S. Code § 107, certain uses of copyrighted material “for purposes such as criticism, comment, news reporting, teaching (including multiple copies for classroom use), scholarship, or research, is not an infringement of copyright.” As a matter of policy, fair use is based on the belief that the public is entitled to freely use portions of copyrighted materials for purposes of commentary and criticism. The fair use privilege is perhaps the most significant limitation on a copyright owner’s exclusive rights. Cyber Defense Media Group is a news reporting company, reporting cyber news, events, information and much more at no charge at our website Cyber Defense Magazine. All images and reporting are done exclusively under the Fair Use of the US copyright act.
Credit: Source link


Comments are closed.